Pass Certified Kubernetes Security Specialist (CKS) Certification Exam With CKS Real Dumps
Do I have any chance to pass Certified Kubernetes Security Specialist (CKS) certification exam? Most candidates asked because of the busy work or no confidence. Let's enhance you skills in real Certified Kubernetes Security Specialist (CKS) exam today. We have released CKS real dumps with the actual exam questions and answers to help you prepare for Certified Kubernetes Security Specialist (CKS) exam successfully and smoothly. If you really intend to take CKS test and looking for the proper Linux Foundation CKS exam dumps, then you can find the best CKS exam questions as the test preparation for Certified Kubernetes Security Specialist (CKS) exam. We ensure that you can pass CKS exam in the first attempt.

What is Certified Kubernetes Security Specialist (CKS) exam?
First of all, every candidate needs to know the Certified Kubernetes Security Specialist (CKS) program was created by the Cloud Native Computing Foundation (CNCF), in collaboration with The Linux Foundation, to help develop the Kubernetes ecosystem. It s a performance-based certification exam that tests candidates' knowledge of Kubernetes and cloud security in a simulated, real world environment.
The Certified Kubernetes Security Specialist (CKS) certification program provides assurance that a CKS has the skills, knowledge, and competence on a broad range of best practices for securing container-based applications and Kubernetes platforms during build, deployment and runtime. Candidates for CKS must hold a current Certified Kubernetes Administrator (CKA) certification to demonstrate they possess sufficient Kubernetes expertise before sitting for the CKS.
What will be tested in the actual CKS exam?
Real Certified Kubernetes Security Specialist (CKS) exam contains 15 questions, which need to be answered in 2 hours. It aims to test your skills on different security aspects as the figure shown:
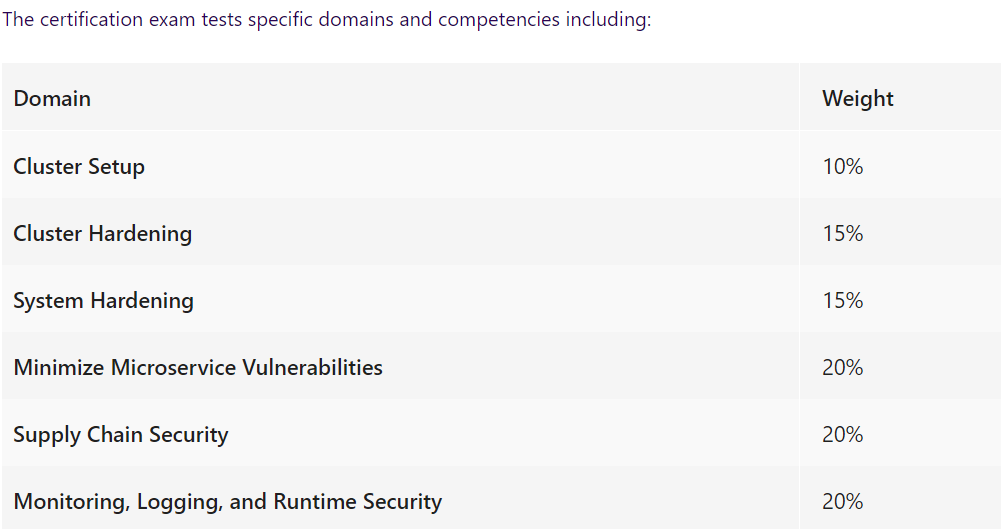
CKS real dumps cover the exam domain, which are high-quality to ensure that you can pass Certified Kubernetes Security Specialist (CKS) certification exam.
Where can candidates find the CKS free dumps online?
Offering CKS free dumps online helps candidates check the high-qaulity of CKS dumps questions. From the demo questions, you can find the CKS exam dumps are real for preparation. You can try to access CKS free dumps post online as shown:
Also, you can read CKS free dumps below:
Create a new NetworkPolicy named deny-all in the namespace testing which denies all traffic of type ingress and egress traffic
Answer:
You can create a "default" isolation policy for a namespace by creating a NetworkPolicy that selects all pods but does not allow any ingress traffic to those pods. ---
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: default-deny-ingress
spec:
podSelector: {}
policyTypes:
- Ingress
You can create a "default" egress isolation policy for a namespace by creating a NetworkPolicy that selects all pods but does not allow any egress traffic from those pods.
---
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: allow-all-egress
spec:
podSelector: {}
egress:
- {}
policyTypes:
- Egress
Default deny all ingress and all egress trafficYou can create a "default" policy for a namespace which prevents all ingress AND egress traffic by creating the following NetworkPolicy in that namespace.
---
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: default-deny-all
spec:
podSelector: {}
policyTypes:
- Ingress
- Egress
This ensures that even pods that aren't selected by any other NetworkPolicy will not be allowed ingress or egress traffic.
Create a network policy named allow-np, that allows pod in the namespace staging to connect to port 80 of other pods in the same namespace.
Ensure that Network Policy:-
1. Does not allow access to pod not listening on port 80.
2. Does not allow access from Pods, not in namespace staging.
Answer:
apiVersion:networking.k8s.io/v1
kind:NetworkPolicy
metadata:
name:network-policy
spec:
podSelector:{} #selects all the pods in the namespace deployed
policyTypes:
-Ingress
ingress:
-ports:#in input traffic allowed only through 80 port only
-protocol:TCP
port:80
Given an existing Pod named nginx-pod running in the namespace test-system, fetch the service-account-name used and put the content in /candidate/KSC00124.txt
Create a new Role named dev-test-role in the namespace test-system, which can perform
update operations, on resources of type namespaces.
Create a new RoleBinding named dev-test-role-binding, which binds the newly created Role to the Pod's ServiceAccount ( found in the Nginx pod running in namespace test-system).
Answer: Send us your feedback on it.
On the Cluster worker node, enforce the prepared AppArmor profile
✑ #include<tunables/global>
✑ profile nginx-deny flags=(attach_disconnected) {
✑ #include<abstractions/base>
✑ file,
✑ # Deny all file writes.
✑ deny/** w,
✑ }
✑ EOF'
Edit the prepared manifest file to include the AppArmor profile.
✑ apiVersion: v1
✑ kind: Pod
✑ metadata:
✑ name: apparmor-pod
✑ spec:
✑ containers:
✑ - name: apparmor-pod
✑ image: nginx
Finally, apply the manifests files and create the Pod specified on it.
Verify: Try to make a file inside the directory which is restricted.
Answer: Send us your Feedback on this.
